Wipe Disk & Shred File
In an earlier posting, Delete Does Not Delete, we've discussed about why deleted files are still possibly recoverable and how to remove their traces permanently by cleaning the disk's free-space. Of the many terms used to describe the 'cleansing', I think "disk wiping" best fit the description.
For those who have used the disk wiping before knew that the process is very lengthy and can take hours to complete. This might not be very practical at times.
Is there other way to destroy file permanently?
Yes, we can 'shred' the file instead. This is analogous to shredding of paper document. Again, there are other terms used to describe this process. Commercial softwares are easily available as well.
If you are using the software introduced earlier (named; Eraser), shredding functionality is readily accessible. There are functions to shred files or shred everything in the Recycle Bin with just few mouse-clicks.
To shred files (using Eraser);
Right-mouse click on the files to be destroyed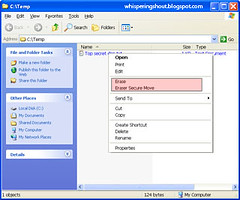
- Select Erase to permanently destroy selected files
To destroy the Recycle Bin's content (using Eraser);
Right-mouse click on the Recycle Bin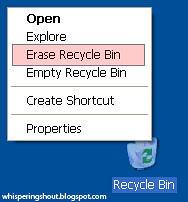
- Select Erase Recycle Bin to permanently destroy everything in the recycle bin
NOTE:
Some document editing software (e.g. Microsoft Word) might periodically creates copies of the document being edited for error recovery purposes. There is no guarantee that the copies will be safely discarded. Therefore, file shredding may not be sufficient to replace disk wiping.
.