TrueCrypt - Disk encryption software
TrueCrypt is an open source, disk encryption software. It works transparently without extra hindrance to the user once the security authentication is validated.
The cryptographic algorithms used are of very high standards. For example, the Advanced Encryption Standard (AES) is adopted by the U.S. government for use in all government departments/agencies to cryptographically protect sensitive information.
TrueCrypt is available at;
TrueCrypt (Please check its license)
http://www.truecrypt.org/
http://www.truecrypt.org/
I am not going to create a step-by-step guide here. You can have such guide after installing the software (go to "Help - User's Guide" menu).
Demystifying Complexities
In the simplest form, there are only 2 major steps required for you to get started;
- Create the 'protection unit' (known as volume)
- Use the volume to save confidential files
Here are some explanations to help your understanding;
- Volume is just disk file that is used by the TrueCrypt. Go ahead and create as many of them as you like. You can always delete them if thing got messed up.
- When creating the volume, you have the option to create a hidden volume inside the volume itself. You can imagine the hidden volume as sub-section of the volume that requires different password to access.
- To use the volume created, you need to mount the volume's file. Refer to user's guide for details
Mounted volume
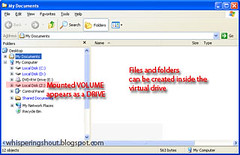
- Upon mounting, the volume can be accessed as a virtual disk DRIVE
Mounting Explained
Mounting Standard Volume
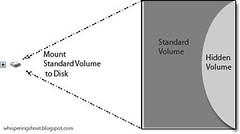
- To mount the standard volume, enter the standard volume's password
- Volume's contents cannot be technically identified without successful login
- If the volume to be mounted contains hidden volume, activate the Hidden Volume Protection feature during login. Failing to do so may risk in damaging the hidden volume when the volume is used
Mounting Hidden Volume
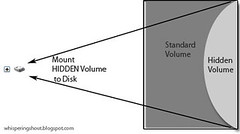
- To mount the hidden volume, enter the hidden volume's password
- Volume's contents cannot be technically identified without successful login
- Each volume can optionally has one Hidden Volume. The hidden volume cannot be identified nor proven exists technically without successful login.
Facts you must know
Strong password is at times cumbersome to use. Why must one use strong password?
The only thing that keeps confidential files away from thieves is the password. Weak password can easily be hacked. On the other hand, using strong password can easily be practised and becomes a habit. More on strong password here.
What can be done if I forgot the volume password(s)?
Well, the only thing you can do is to bid your files goodbye. You can try to hack the security using brute force hacking. But, based on current technological capability, it can take thousands or millions of years depending on the strength of the password used.
.
0 shouts:
Post a Comment